App Configuration for Microsoft Connection in MS Portal for OAuth 2.0
This support article provides instructions for configuring the Application and its permissions required to create connection in Provar for MS Exchange and MS Graph Connection types.
Until now, Provar had been using basic authentication for Microsoft Exchange Web Service (EWS). Provar users can now access Microsoft Emails using OAuth 2.0 using Microsoft (EWS) and MS Graph by creating a new connection or updating an existing connection. And you can use Send and Subscribe Test APIs with Microsoft Connection for emails.
Provar Application registration in Azure Active Directory (AD)
To register an application in Azure AD:
- Log into aad.portal.azure.com with the appropriate admin account.
- Click Azure Active Directory in the menu.
- Under the Manage section, click App Registrations.
- Click New Registration.
- In the Name field, enter a name to register the new application.
- Set Supported account types as appropriate.
- Click Register.
The Provar Application is registered.
Configure permissions in Azure Active Directory
To configure permissions in the Azure Active Directory:
1. In App registrations, select the application registered in the previous section.
2. Under Manage, click API Permissions.
3. Click Add a permission.
4. Under my organization’s APIs, type “office” in the search box and select Office 365 Exchange Online.
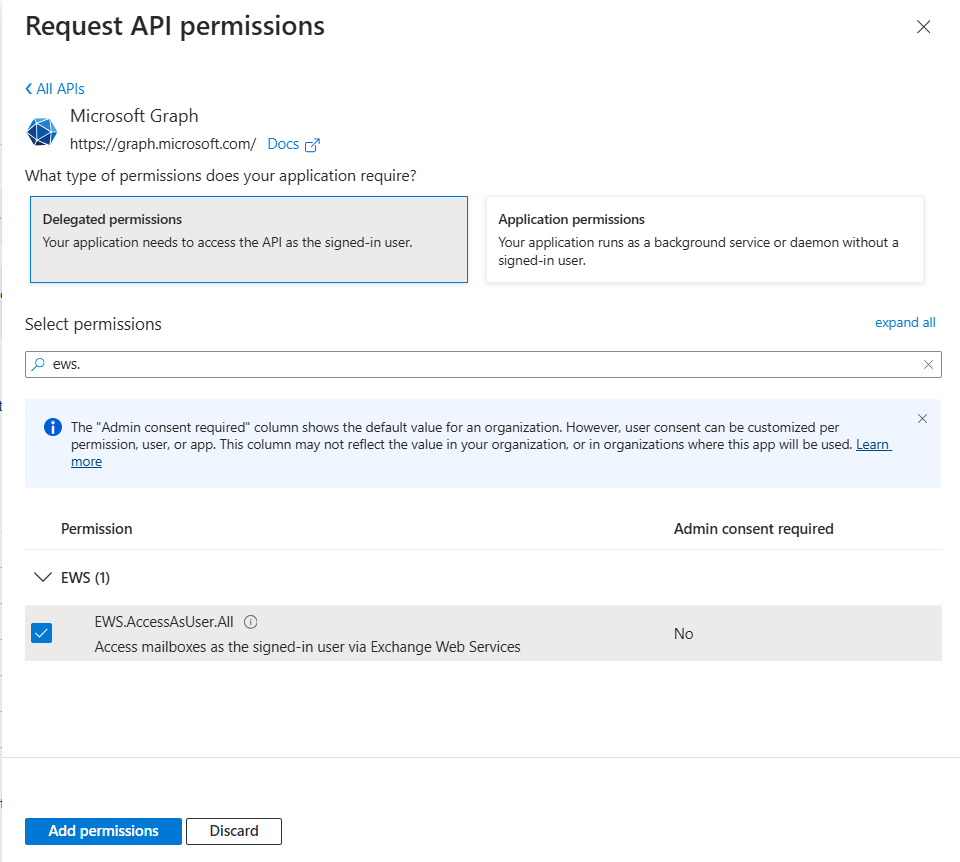
5a. If you are using EWS Exchange Web Service, then use these permissions.
You need to add a delegated EWS.AccessAsUser.All permission and Mail.Read and Mail.Send as Application Type permission.
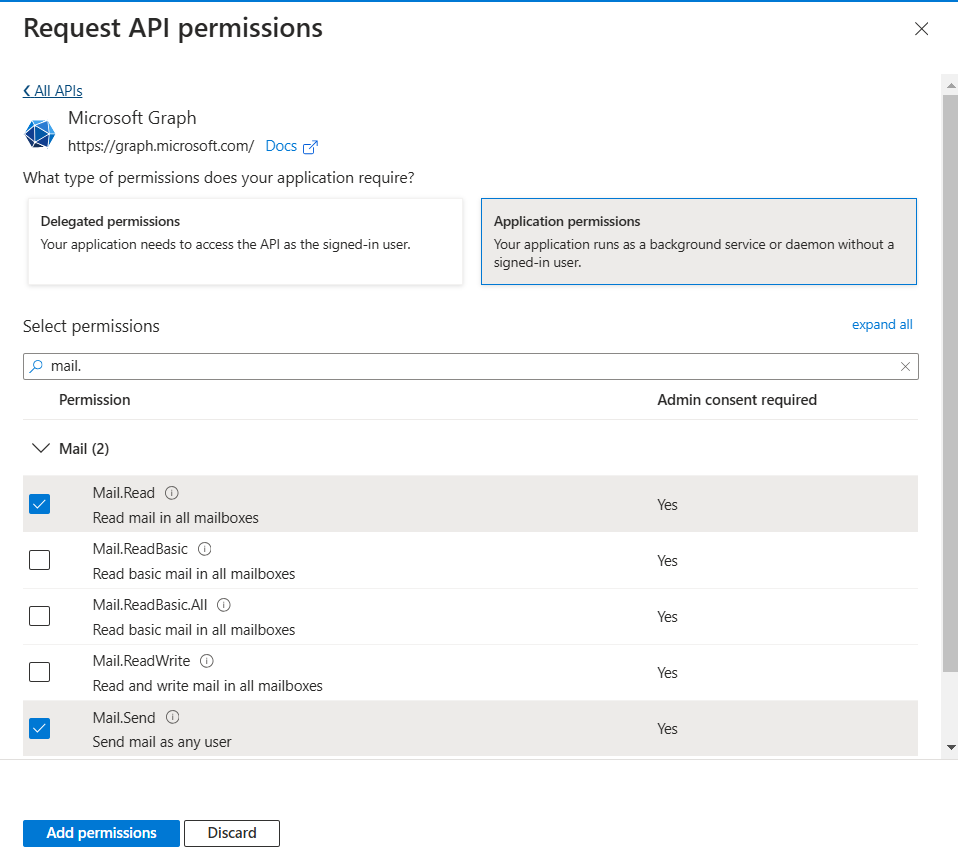
5b. If you are using MS Graph, then use these permissions.
All permissions should be Application type permissions.
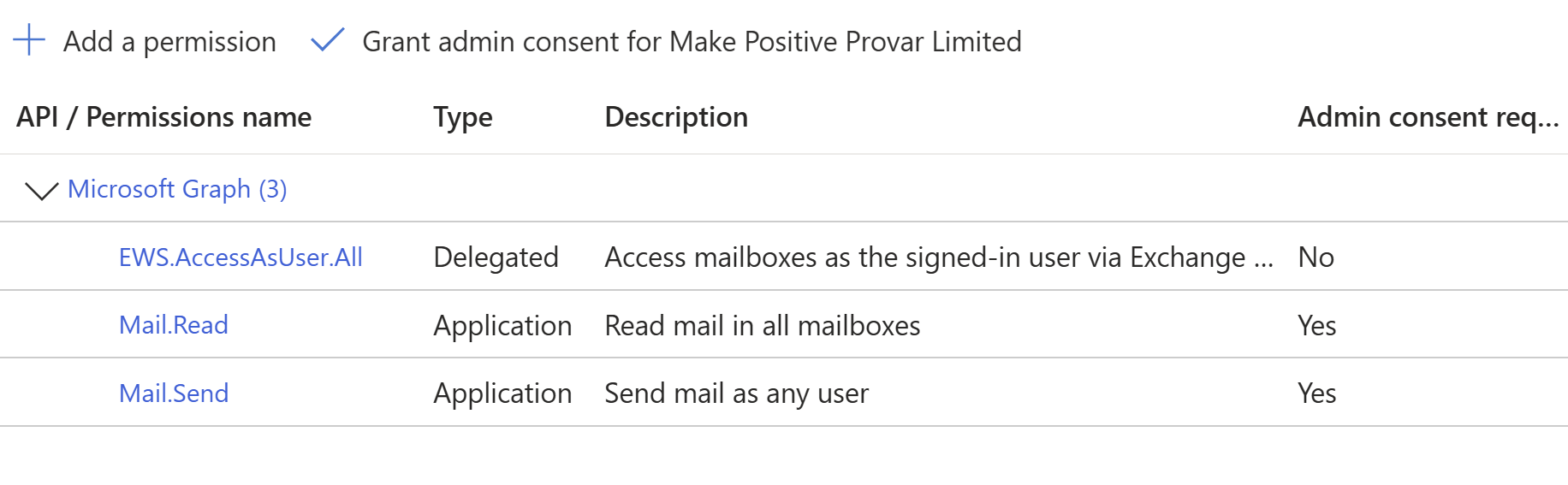
6. Click Done.
7. Under Grant Consent, select Grant admin consent for (your domain here).
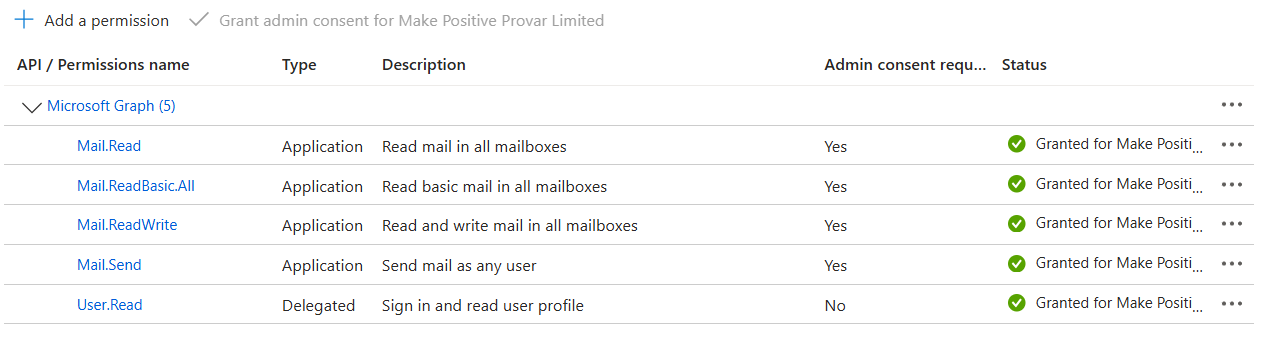
8. Select Yes. The permissions are displayed in a list.
9. Under Manage, click Certificates & secrets.
10. Select New Client Secret. In the Expire field, select an appropriate expiration duration. Click Save.
11. A value is displayed. Copy this value and make a note since this is the only time this value is displayed.
12. From the Overview section, copy the Application ID and Tenant ID to add to the EWS configuration.
13. To get the Redirect URI, click on Add a Redirect URI, as shown in the above screenshot.
14. Click Add a Platform.
15. Select Web from the Web Application section.
16. Enter the Redirect URI e.g. https://oauth.pstmn.io/v1/browser-callback
18. Click Configure. The screenshot given below shows the Redirect URI.
- Home
- Get Started with V2
- Using Provar
- Understanding Provar’s Use of AI Service for Test Automation
- Provar Automation
- Creating a New Test Project
- Import Test Project from a File
- Import Test Project from a Remote Repository
- Import Test Project from Local Repository
- Commit a Local Test Project to Source Control
- Salesforce API Testing
- Behavior-Driven Development
- Consolidating Multiple Test Execution Reports
- Creating Test Cases
- Custom Table Mapping
- Functions
- Debugging Tests
- Defining a Namespace Prefix on a Connection
- Defining Proxy Settings
- Environment Management
- Exporting Test Projects
- Exporting Test Cases into a PDF
- Japanese Language Support
- Override Auto-Retry for Test Step
- Customize Browser Driver Location
- Mapping and Executing the Lightning Article Editor in Provar
- Managing Test Steps
- Namespace Org Testing
- NitroX
- Provar Test Builder
- ProvarDX
- Refresh and Recompile
- Reintroduction of CLI license Check
- Reload Org Cache
- Reporting
- Running Tests
- Searching Provar with Find Usages
- Secrets Management and Encryption
- Setup and Teardown Test Cases
- Tags and Service Level Agreements (SLAs)
- Test Cycles
- Test Plans
- Testing Browser – Chrome Headless
- Testing Browser Options
- Tooltip Testing
- Using the Test Palette
- Using Custom APIs
- Callable Tests
- Data-Driven Testing
- Page Objects
- Block Locator Strategies
- Introduction to XPaths
- Creating an XPath
- JavaScript Locator Support
- Label Locator Strategies
- Maintaining Page Objects
- Mapping Non-Salesforce Fields
- Page Object Operations
- ProvarX™
- Refresh and Reselect Field Locators in Test Builder
- Using Java Method Annotations for Custom Objects
- Applications Testing
- Database Testing
- Document Testing
- Email Testing
- Email Testing in Automation
- Email Testing Examples
- Gmail Connection in Automation with App Password
- App Configuration for Microsoft Connection in MS Portal for OAuth 2.0
- OAuth 2.0 Microsoft Exchange Email Connection
- Support for Existing MS OAuth Email Connection
- OAuth 2.0 MS Graph Email Connection
- Create a Connection for Office 365 GCC High
- Mobile Testing
- OrchestraCMS Testing
- Salesforce CPQ Testing
- ServiceMax Testing
- Skuid Testing
- Vlocity API Testing
- Webservices Testing
- DevOps with V2
- Introduction to Provar DevOps
- Introduction to Test Scheduling
- Apache Ant
- Configuration for Sending Emails via the Automation Command Line Interface
- Continuous Integration
- AutoRABIT Salesforce DevOps in Provar Test
- Azure DevOps
- Running a Provar CI Task in Azure DevOps Pipelines
- Configuring the Automation Secrets Password in Microsoft Azure Pipelines
- Parallel Execution in Microsoft Azure Pipelines using Multiple build.xml Files
- Parallel Execution in Microsoft Azure Pipelines using Targets
- Parallel Execution in Microsoft Azure Pipelines using Test Plans
- Bitbucket Pipelines
- CircleCI
- Copado
- Docker
- Flosum
- Gearset
- GitHub Actions
- Integrating GitHub Actions CI to Run Automation CI Task
- Remote Trigger in GitHub Actions
- Parameterization using Environment Variables in GitHub Actions
- Parallel Execution in GitHub Actions using Multiple build.xml Files
- Parallel Execution in GitHub Actions using Targets
- Parallel Execution in GitHub Actions using Test Plan
- Parallel Execution in GitHub Actions using Job Matrix
- GitLab Continuous Integration
- Travis CI
- Jenkins
- Execution Environment Security Configuration
- Provar Jenkins Plugin
- Parallel Execution
- Running Provar on Linux
- Reporting
- Salesforce DX
- Git
- Version Control
- Salesforce Testing
- Recommended Practices
- Salesforce API Access Control Security Update – Impact on Provar Connections
- Salesforce Connection Best Practices
- Improve Your Metadata Performance
- Java 21 Upgrade
- Testing Best Practices
- Automation Planning
- Supported Testing Phases
- Provar Naming Standards
- Test Case Design
- Create records via API
- Avoid using static values
- Abort Unused Test Sessions/Runs
- Avoid Metadata performance issues
- Increase auto-retry waits for steps using a global variable
- Create different page objects for different pages
- The Best Ways to Change Callable Test Case Locations
- Working with the .testProject file and .secrets file
- Best practices for the .provarCaches folder
- Best practices for .pageObject files
- Testing Best Practices
- Troubleshooting with V2
- How to Use Keytool Command for Importing Certificates
- Browsers
- Configurations and Permissions
- Add Permissions to Edit Provar.ini File
- Configure Provar UI in High Resolution
- Enable Prompt to Choose Workspace
- Increase System Memory for Provar
- Refresh Org Cache Manually
- Show Hidden Provar Files on Mac
- Java Version Mismatch Error
- Unable to create test cases, test suites, etc… from the Test Project Navigation sidebar
- Connections
- DevOps with V2
- Error Messages
- Provar Manager 3.0 Install Error Resolution
- Provar Manager Test Case Upload Resolution
- Administrator has Blocked Access to Client
- JavascriptException: Javascript Error
- Resolving Failed to Create ChromeDriver Error
- Resolving Jenkins License Missing Error
- Resolving Metadata Timeout Errors
- Test Execution Fails – Firefox Not Installed
- Selenium 4 Upgrade
- Licensing and Installation
- Memory
- Test Builder
- V2 Release Notes